This section summarizes the main requirements and principles regulating the assignment of IP addresses which are used in your Azure cloud infrastructure, to which you will deploy CloudBlue Commerce.
Requirements and principles
Public IPs:
- For nodes which need to respond to external requests (such as DNS nodes, for example), it is necessary to assign static public IP addresses. Azure uses the Network Address Translation (NAT) mechanism to allow Azure virtual machines to communicate with the Internet through a public IP address.
- Each proxy node must have a static public IP address.
AKS cluster:
- The AKS cluster must be deployed using the "Basic" network configuration mode. In such a case, Kubernetes nodes will be created in a dedicated VNet.
- For connectivity between Virtual Machines from IAAS VNet and the automatically created VNet of the AKS cluster, VNet peering must be configured. For more detail, please see Building Your Azure Cloud Infrastructure.
- For connectivity between the Operations management node (which is located in the IAAS VNet) and Kubernetes services from the AKS cluster, a VPN tunnel from the Operations management node to the OpenVPN service in the AKS cluster must be created. For more detail, see Configuring the Virtual Machine for the Operations Management Node.
- If IAAS VNet does not use subnet ranges assigned to AKS cluster with "Basic" network by default, you can create AKS in Azure portal. When it is necessary to use some specific IP ranges in the AKS cluster, the AKS cluster must be deployed as described in Deploying an AKS Cluster with Custom IP Ranges.
-
The following IP ranges must not be used for AKS cluster: 169.254.0.0/16, 172.30.0.0/16, 172.31.0.0/16
Note: Default AKS IP ranges are listed in the table below.
-
If IAAS VNet must contain subnets in 10.x IP ranges, you can configure several address ranges in IAAS VNet and make sure that they do not overlap with AKS subnets (see the picture below). You can also adjust AKS VNet, which can be found in resource group automatically generated for AKS resources. VNet peering can be configured only in case if VNets do not intercept with each other by their address ranges.
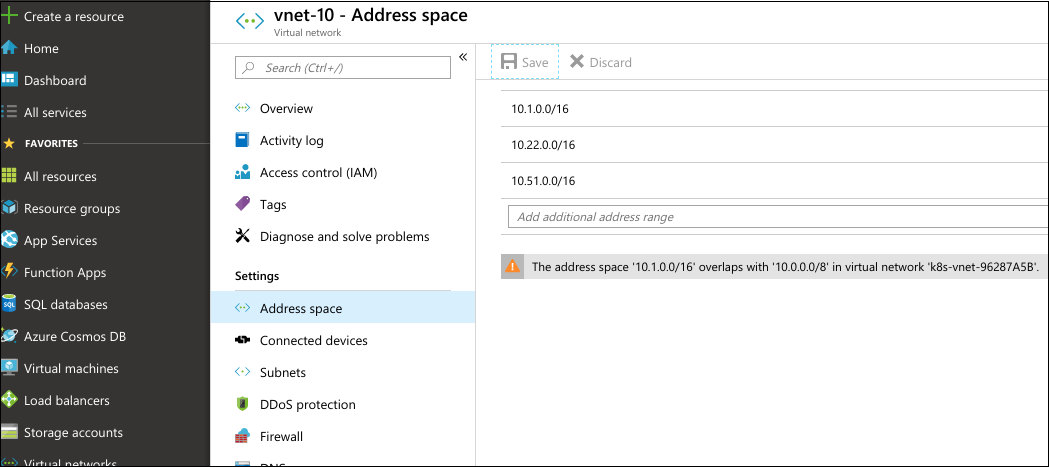
Other:
-
(optional) For easier resource management, it is highly recommended that your IP address ranges belong to a single VNet and have enough space to contain all nodes that belong to a specific network zone. When defining IP ranges, it is important to keep in mind which nodes must belong to which subnet. Below is an example of how to define IP ranges.
Example: Defining IP ranges. Part 1
The VNet address range is 172.18.0.0/17 (172.18.0.1-172.18.127.254):
Subnet
Range
First and last address
Frontnet zone
172.18.0.0/21
172.18.0.1 - 172.18.7.254
Backnet-IAAS zone, for standalone VMs
172.18.8.0/21
172.18.8.1 - 172.18.15.254
DBnet zone
172.18.24.0/21
172.18.24.1 - 172.18.31.254
Adminnet zone
172.18.16.0/21
172.18.16.1 - 172.18.23.254
GatewaySubnet
172.18.127.224/27
172.18.127.225 - 172.18.127.254
-
There are also several additional subnets that you may need to set when creating Azure cloud infrastructure resources (see the table below). Due to Azure's specifics, the IP addresses for the subnets below must be outside all the defined VNet address ranges.
Example: Defining IP ranges. Part 2
Subnet
Range
First and last address
Point-to-site VPN clients
192.168.18.0/25
192.168.18.1 - 192.168.18.126
Backnet-AKS-services*
10.0.0.0/16
10.0.0.1 - 10.0.255.254
Backnet-AKS-pods*
10.244.0.0/16
10.244.0.1 - 10.244.255.254
Backnet-AKS-nodes zone, for AKS cluster nodes*
10.240.0.0/16
10.240.0.1 - 10.240.255.254
AKS Docker subnet 172.17.0.0/16 172.17.0.1 - 172.17.255.254 *The specified IP range is defined automatically when an AKS cluster is deployed using the ready-made ARM template or via Azure portal (without customizing IP ranges). To deploy an AKS cluster with custom IP ranges, please see Deploying an AKS Cluster with Custom IP Ranges.
Related Topics