Table Of Contents
Application Packaging Standard
Last updated 18-Mar-2019Security Model¶
APS security model includes various mechanisms to protect APS applications, resources, and the platform as a whole.
In this document:
Authentication¶
APS controller, as the APS bus authority, interacts through the secure HTTPS protocol with other APS participants (actors) on the APS bus using a secure authentication of every actor.
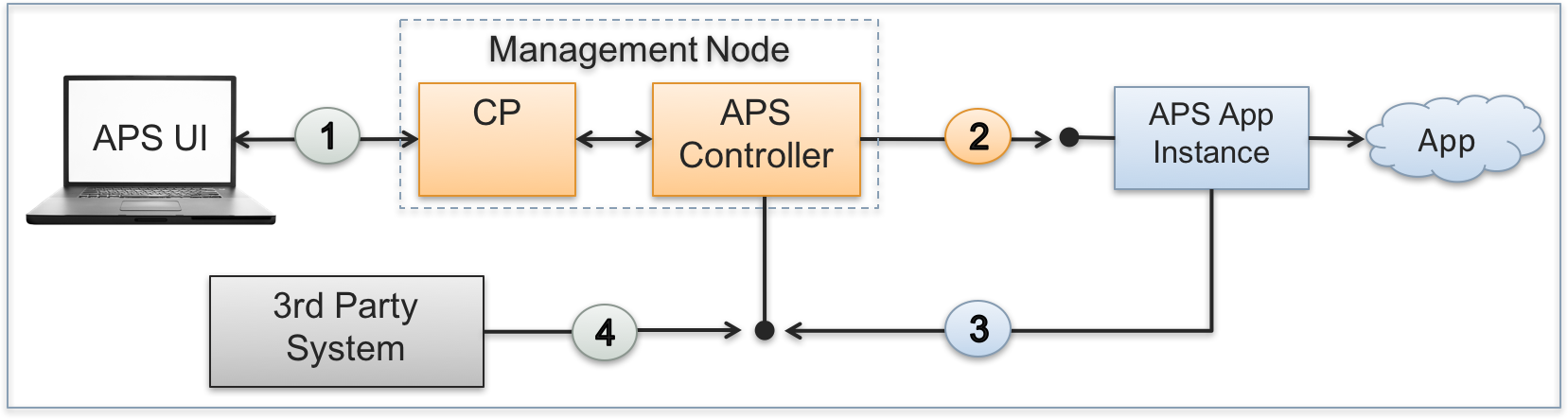
There are the following interactions on the bus:
Platform built-in and custom UI scripts can send REST requests to the APS controller and receive notifications sent from the APS controller on behalf of APS applications. The respective sessions are set up on behalf of the user who is interacting with the platform control panel (CP) at the moment. The CP authenticates users when they log in. This makes all subsequent REST requests sent from the UI to the APS controller authenticated through the platform built-in internal mechanism.
The APS controller can send a REST request to an APS application instance using one of authentication protocols:
- By default, the APS controller uses authentication through SSL certificates. For this purpose, it generates a pair of X509 certificate and private key for every APS application instance when installing the latter. During the same installation process, the APS controller sends its own SSL certificate to the newly created APS application instance. This allows an APS application instance to authenticate the APS controller in the incoming REST requests because they must be signed by that SSL certificate.
- The other way is based on the OAuth protocol that must be explicitly specified in a REST request sent through the APS controller. The receiving APS application instance must be preliminary configured for the use of a shared OAuth key and secret pair.
When forwarding a request from an actor to an APS application instance, the APS controller adds the APS-Actor-ID header to specify the actor.
An APS application instance can send its own REST request to the APS controller. The authentication goes through the method that was used initially by the APS controller (see the previous item), either SSL or OAuth.
The provider can allow a 3rd party actor (an external management system, a custom script, or a GUI REST client) to interact with the platform services through the APS controller as explained in Using Platform Services. An actor must authenticate itself by the OAuth protocol using a shared pair of a key and secret as explained in Using APS REST API.
Authorization¶
Once the opposite side is authenticated, the APS controller defines the operations allowed for the interacting actor. The authorization mechanism defines what operations over a resource or a resource property are allowed for a certain actor. It is based on the following key points.
- The APS controller acts on behalf of the platform and thus is allowed to perform any REST operations exposed by application services.
- The APS controller authorizes an APS application instance for any REST operations over resources provisioned from that application instance.
- The APS controller authorizes a user for REST operations over a resource depending on the following settings:
- The user role in the account hierarchy, that is whether the user presents an end-user or one of accounts (provider, reseller, or customer) as described in Security Roles.
- The user’s or account’s relationship with the resource, that is whether the user or account is the resource owner or has another relationship with it as described in Security Roles.
- Access definition in the resource as described in Access Rights Policy.
- An APS application can impersonate a customer by sending the APS-Resource-ID header to operate APS resources of other applications used by the customer. For example, an application needs to configure a DNS zone. This impersonation influences only the authorization process and has nothing to do with authentication.
Confidentiality¶
While the authorization makes some resources, methods, and properties available to certain actors, it is also possible to hide values of some properties from human eyes without prohibiting the use of them. This typically concerns passwords, security keys, and other sensitive properties.
For this purpose, APS provides the encrypted attribute that you can assign to a confidential property.
Custom Privileges¶
The platform allows APS applications to register their own privileges on
the objects (resources, properties, and operations) authorized through the access attribute.