Granting Permissions
To grant the required API permissions to the application, complete the following steps:
-
Select the configured Azure application and click API permissions.
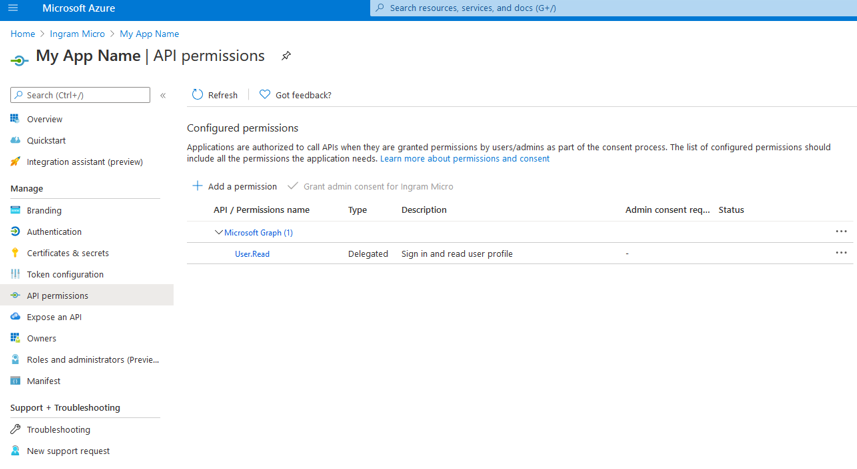
- Click Add a permission and select the type of permission you wish to add: Microsoft Graph, Azure Service Management, etc.
- Select Delegated Permissions or Application permissions, as required (see the table below).
-
Select the required permissions specified in the following table and click Add Permissions. To make it easier to find API permissions, you can search by id instead of by name (see the image below).
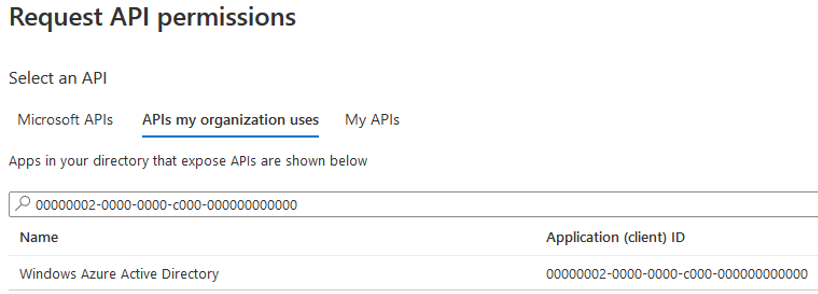
| API Name / ID | Permissions | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
|
Azure Active Directory Graph https://graph.windows.net/ 00000002-0000-0000-c000-000000000000 |
|
||||||||||
|
Azure Service Management https://management.azure.com/ 797f4846-ba00-4fd7-ba43-dac1f8f63013 |
|
||||||||||
|
Microsoft Partner Center https://reseller.microsoft.com fa3d9a0c-3fb0-42cc-9193-47c7ecd2edbd |
|
||||||||||
|
Microsoft Partner https://api.partner.microsoft-int.com 4990cffe-04e8-4e8b-808a-1175604b879f |
|
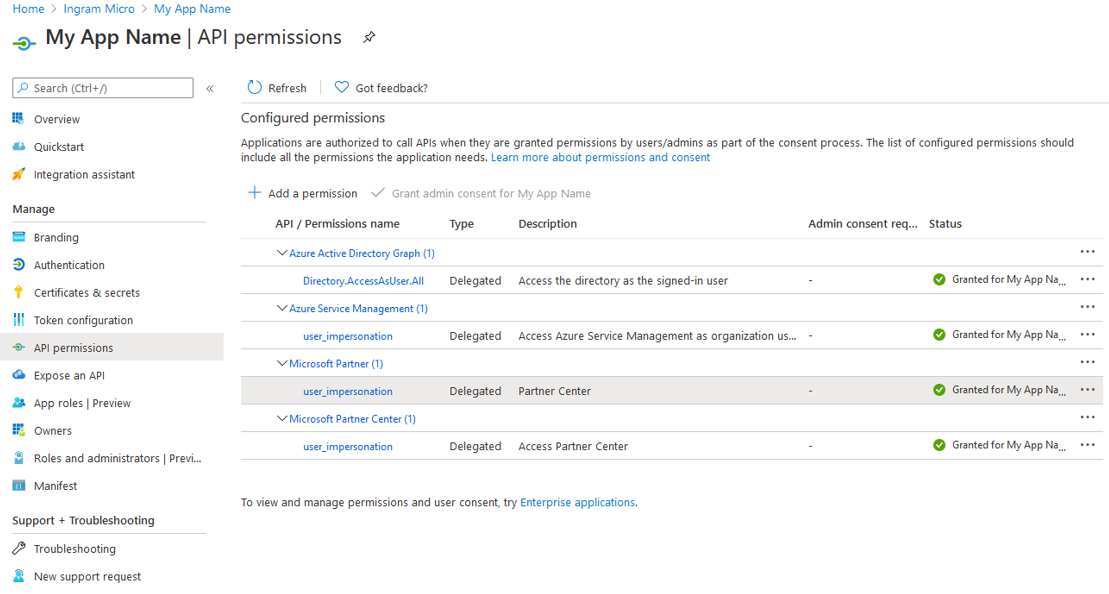
Important: Make sure you click the Grant admin consent for {My App Name} button once permissions have been included.